A Phishing Frenzy: Fake WordPress Security Advisories and Backdoor Infiltration
This article delves into a recent phishing campaign targeting WordPress users. The campaign utilizes deceptive emails claiming a fictitious vulnerability (CVE-2023-45124) to trick unsuspecting administrators into installing a malicious plugin. This plugin, disguised as a security patch, establishes a backdoor, granting attackers unauthorized access and control over compromised websites. The paper explores the technical details of the campaign, analyzes the potential consequences, and outlines crucial preventative measures for WordPress administrators.
Introduction:
WordPress, a widely used content management system (CMS), powers millions of websites globally. Its popularity makes it a prime target for cybercriminals who employ various tactics to exploit vulnerabilities and compromise user data. Phishing campaigns are a prevalent threat, and WordPress administrators are particularly susceptible due to their privileged access and responsibility for website security.
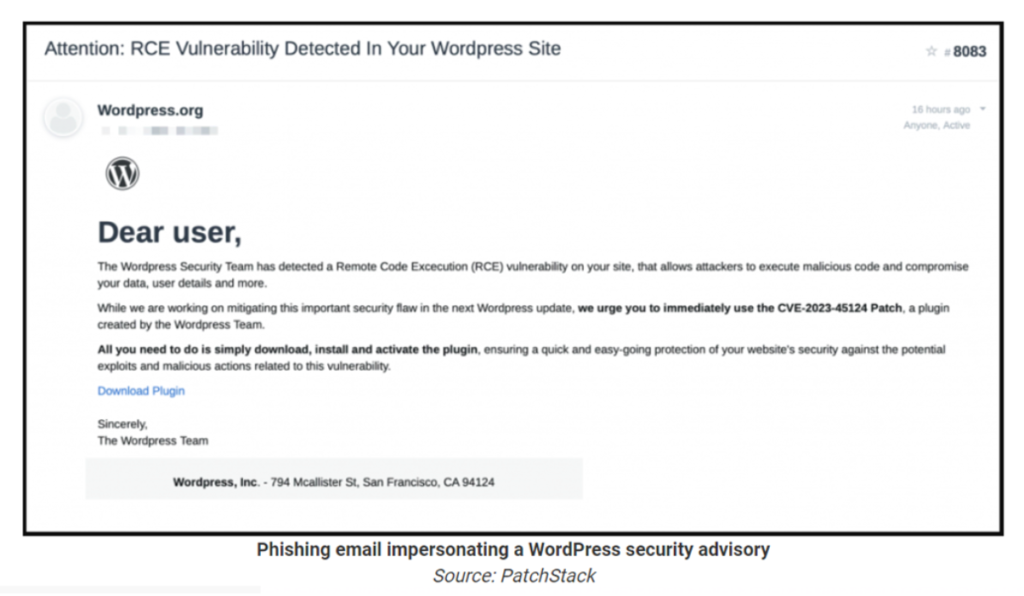
The Deceptive Facade: Unmasking the Phishing Campaign
This recent phishing campaign leverages social engineering tactics to deceive WordPress administrators. Attackers craft emails masquerading as official WordPress security advisories. These emails typically highlight a non-existent vulnerability, such as the fabricated CVE-2023-45124, and urge recipients to download and install a security patch to address the fictitious threat. The emails often utilize urgency and fear, prompting administrators to take immediate action without proper verification.
The Malicious Payload: Unveiling the Backdoor Plugin
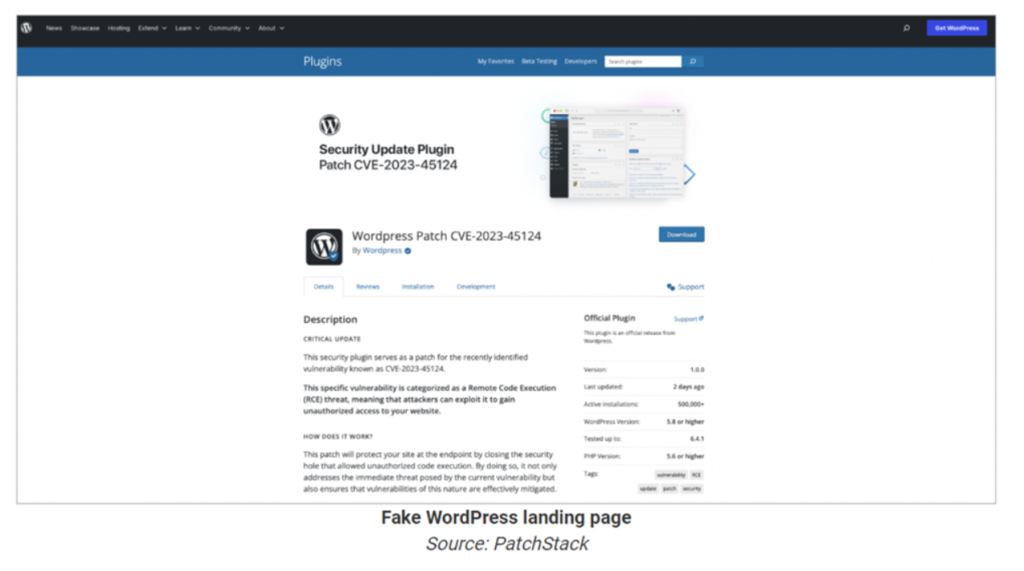
The deceptive emails in this campaign often include a link directing administrators to a fake website that closely resembles the legitimate WordPress download page. This website houses the malicious plugin, disguised as a security patch and named with deceptive titles like "wp-securitypatch." Once downloaded and installed, the plugin activates a series of detrimental actions.
- Hidden Admin User Creation: The plugin surreptitiously creates a new admin user account on the compromised website. This account, often named "wpsecuritypatch," provides the attackers with illegitimate administrative access, allowing them to modify website content, steal sensitive data, or even install additional malware.
- Backdoor Establishment: The plugin establishes a backdoor on the compromised website. A backdoor is essentially a hidden channel that enables remote access to the website's functionalities. This grants attackers persistent control, allowing them to manipulate the website unseen, inject malicious code, or launch further attacks against the server.
- Data Exfiltration: Backdoor functionality often includes capabilities such as file management and SQL client access. Using these features, attackers can potentially extract sensitive information such as usernames, passwords, customer data, or website content.
The Potential Impact: A Spectrum of Threats
The consequences of falling victim to this phishing campaign can be severe for website owners and administrators.
- Website Defacement: Attackers with backdoor access can deface the website, altering its content and potentially displaying malicious messages or propaganda.
- Search Engine Optimization (SEO) Poisoning: Attackers might inject malicious code into the website, manipulating search engine algorithms to rank the website higher for specific keywords. This can attract unsuspecting users to the compromised website, potentially leading to further attacks like malware distribution or phishing scams.
- Data Breach: Backdoor access opens the door for attackers to steal sensitive information like user credentials, financial data, or customer details. This can lead to identity theft, financial losses, and reputational damage for the website owner.
- Spam Injection: Attackers can manipulate the website to inject spammy content, redirecting users to phishing websites or malicious advertisements. This can negatively impact user experience and potentially damage the website's reputation.
Fortifying Defenses: Strategies to Mitigate the Threat
Combating these phishing tactics requires a multi-layered approach incorporating technological solutions and user awareness campaigns. Here are some critical preventative measures for WordPress administrators:
- Scrutinize Incoming Emails: Never click on links or download attachments from unsolicited emails, especially those claiming urgent security issues. Always verify the email sender's legitimacy. Legitimate security advisories from WordPress will likely be posted on their official website or communicated through official channels.
- Official Sources Only: Always seek security updates directly from the WordPress website or official repositories.
- Strong and Unique Passwords: Implement strong, unique passwords for all WordPress administrator accounts. Consider employing multi-factor authentication (MFA) for an extra layer of security.
- Regular Backups: Maintain regular backups of your website's files and database. In the event of a compromise, a recent backup can help restore the website to a clean state.
- Security Plugins: Utilize reputable security plugins that can scan for vulnerabilities, detect malware, and block suspicious activity. Regularly update these plugins to ensure they have the latest security patches.
- User Education: Educate all website administrators and personnel involved in managing the website about phishing scams. Train them to identify suspicious emails and the importance of verifying information